The recent exploit with the malicious polyfill library highlights a critical gap in the capabilities of most Software Composition Analysis (SCA) tools. Widely used to ensure compatibility across different browsers, Polyfills can pose significant security risks when hosted on Content Delivery Networks (CDNs). Threatrix has long supported the security of CDN-referenced open source, detecting a wide range of open-source components and assets often missed by other SCA tools, thereby closing significant security gaps.
Threatrix Blog
Enterprise open source security & compliance
Results for:
ClearCategory: OPEN SOURCE SECURITY
Clear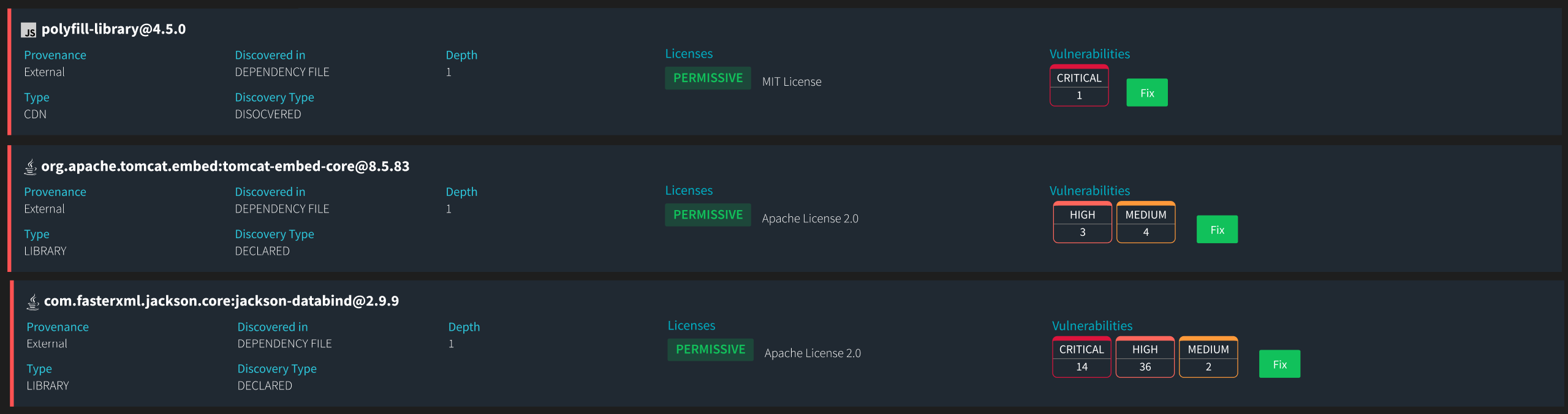
The European AI Act, developed after extensive legislative deliberation, is the first comprehensive regulation for artificial intelligence systems, including general-purpose AI models (GPAIMs). Given the European Union’s proactive stance on technology regulation, developers and users worldwide should closely examine the AI Act's requirements and exceptions, particularly those related to open-source technologies. This understanding will be essential as similar regulations are likely to emerge globally in the near future.

As we continue into 2024, the importance of Software Composition Analysis (SCA) tools has reached a new peak. The best-in-class SCA solutions offer unparalleled automation that saves developers and compliance teams time and organizational costs as we enter the new realm of AI coding tools. By using SCA tools, companies can automate detecting outdated or vulnerable open-source libraries and ensure that any open-source licenses are compatible with their project policies. This proactive approach helps mitigate legal risks associated with license non-compliance and reduces the threat of security breaches from known vulnerabilities in open-source components.

Software development is not just about creating code but ensuring that it complies with various open source regulatory and security standards. As software supply chains become more complex with AI development tools and intertwined with open-source components and third-party services, robust supply chain compliance has never been more critical.
As the ecosystem of open source software continues to expand, it brings opportunities and threats that can pose significant challenges to corporate security infrastructure. One such threat that often gets overshadowed is the technical debt that accumulates from using outdated open source components in software development. Outdated components are a common, invisible menace.

Software development is evolving at a breakneck pace, with developers under increasing pressure to deliver projects faster and more efficiently. As a result, they are turning to tools like StackOverflow, Unity Answers, Github, and AI-based tools like ChatGPT and Github co-pilot to reduce development time and improve efficiency.

Software composition analysis (SCA) tools are becoming increasingly popular for managing the security risks associated with open source software. These tools help identify and mitigate potential vulnerabilities and other security issues in open source components used to build applications. While many SCA tools focus on scanning the final built code, the importance of build-time scans […]