 | Please excuse the transition to our new website design.
| Please excuse the transition to our new website design.
 | Please excuse the transition to our new website design.
| Please excuse the transition to our new website design.
Find vulnerabilities, in more than 400 languages, early in your development lifecycle by integrating Threatrix open source vulnerability detection into your existing tool suite



Pull request integration creates a seamless, uninterrupted workflow for developers. Ultra-fast security analysis won't slow down your team and Threatix policy management makes it easy to enforce policies for a single project or thousands of projects across hundreds of teams.




Threatrix finds security vulnerabilities in legacy code by easily integrating with all of your legacy SCM tools. With a few clicks Threatrix will scan your legacy repositories, report on imminent threats, and automate your response and remediation.
We maintain comprehensive vulnerability data across 400 languages from every known public repository including NVD, NPM Security, Rubygems Redhat Security, Alpine security among numerous others
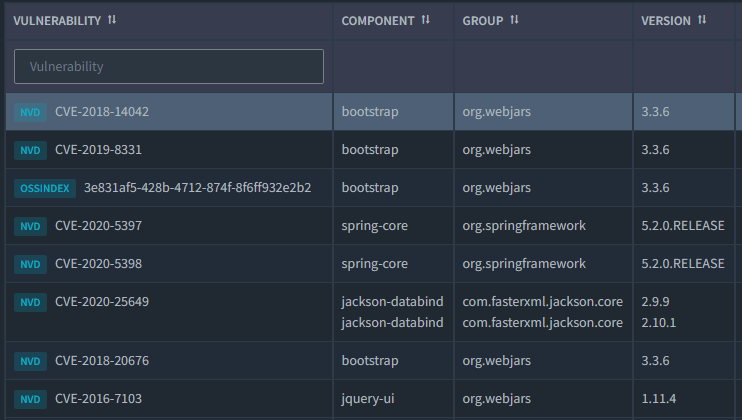
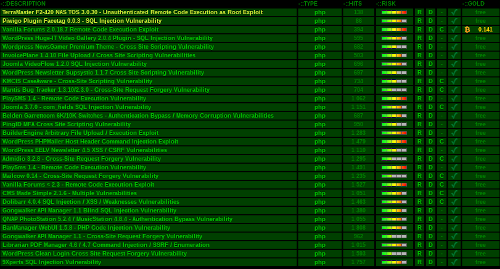
While public databases of vulnerabilities are necessary, we must remain diligent. Our first to market technology employs machine learning to search petabytes of dark web data searching for vulnerabilities in open source libraries.
Vulnerability remediation is a snap with library secure version advice for each vulnerable component. Available from our dashboard or within your SCM, as annotations, saving your developers time and reducing MTTR by up to 95%.
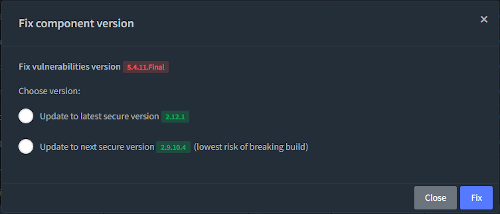
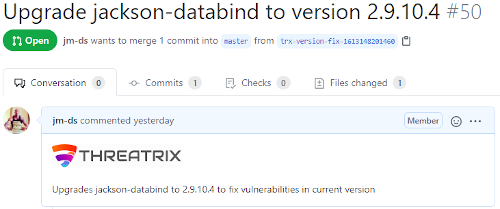
Risk reduction should be simple. With one click your vulnerable dependency will be upgraded to a secure version. A pull request will be created on a new branch so that your developers can test the change before merging the change into your development branch.
Automating the detection of open source vulnerabilities, licenses, and supply chain risk and quality is a snap. We seamlessly integrate into tons of build tools and can quickly deliver risk remediation suggestions











