The recent exploit with the malicious polyfill library highlights a critical gap in the capabilities of most Software Composition Analysis (SCA) tools. Widely used to ensure compatibility across different browsers, Polyfills can pose significant security risks when hosted on Content Delivery Networks (CDNs). Threatrix has long supported the security of CDN-referenced open source, detecting a wide range of open-source components and assets often missed by other SCA tools, thereby closing significant security gaps.
Threatrix Blog
Enterprise open source security & compliance
Results for:
Clear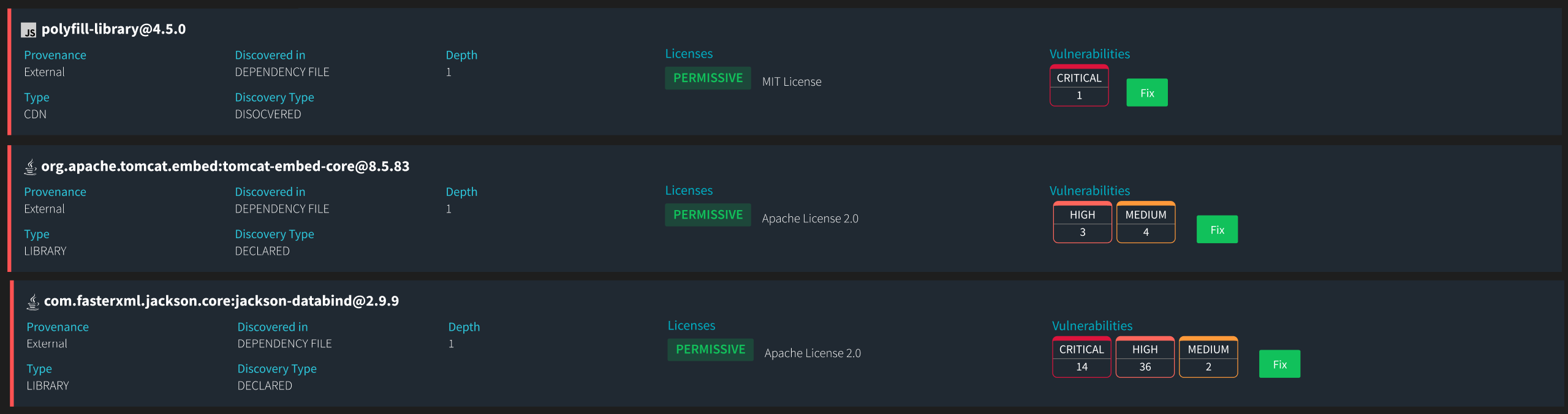

AI code detection tools are crucial for ensuring open source license compliance and extensive code base analysis. Meanwhile, AI-generated code is a valuable developer tool, enhancing productivity by automating routine coding tasks, offering optimized code suggestions, and suggesting optimized code snippets. Our essential guide delves into AI-generated code detection tools, their importance, key features, and how they can enhance development workflows. We will also explore how Threatrix is a comprehensive solution for managing these challenges.

Detecting AI-generated code is increasingly vital as artificial intelligence shapes the future of software development. This comprehensive guide for 2024 delves into the significance of identifying AI-generated code and the essential considerations for developers to maintain compliance and avoid legal complications. We highlight the importance of understanding open source licensing origins, attribution requirements, and compatibility between the different licenses.
you select an open-source license, you define the terms under which others can use your software. This decision impacts how freely others can use your code and how modifications and redistributions are handled. However, making the wrong choice can lead to legal challenges and restrict the intended use of your software, potentially causing significant setbacks to your project.
The European AI Act, developed after extensive legislative deliberation, is the first comprehensive regulation for artificial intelligence systems, including general-purpose AI models (GPAIMs). Given the European Union’s proactive stance on technology regulation, developers and users worldwide should closely examine the AI Act's requirements and exceptions, particularly those related to open-source technologies. This understanding will be essential as similar regulations are likely to emerge globally in the near future.

As we continue into 2024, the importance of Software Composition Analysis (SCA) tools has reached a new peak. The best-in-class SCA solutions offer unparalleled automation that saves developers and compliance teams time and organizational costs as we enter the new realm of AI coding tools. By using SCA tools, companies can automate detecting outdated or vulnerable open-source libraries and ensure that any open-source licenses are compatible with their project policies. This proactive approach helps mitigate legal risks associated with license non-compliance and reduces the threat of security breaches from known vulnerabilities in open-source components.

License compliance for AI-generated code has become crucial as AI continues to reshape software development, driving innovation and increasing complexity. In 2024, the integration of AI in creating functional code is now a standard in software engineering, intensifying challenges related to open source licensing and attribution. This complexity necessitates robust software composition analysis tools to manage compliance effectively, ensuring that innovations do not breach intellectual property laws or open-source legal requirements. As AI developer tools like chatbots and code assistants evolve and use extensive existing code bases, including vast amounts of open-source, they highlight the importance of accurate attribution and compliance with licensing. This scenario underscores the need for developers and corporations to adopt a nuanced approach to legal and ethical issues in software development, requiring more than just technical skills but a deep understanding of the legal landscape.
-
...