Open source software (OSS) is integral to modern software development, offering flexibility, cost-effectiveness, and accelerated innovation but ensuring adherence with the attached licenses is a critical concern for all organizations with the use of these components because they impose certain obligations and restrictions on the use, modification, distribution, and sharing of software. Non-compliance with these licenses can result in legal consequences, including copyright infringement claims, loss of intellectual property rights, and damaged reputations. While all organizations with developers find OSS easy to consume, adherence management is problematic.
Tesla released a portion of their Autopilot intellectual property due to the use of the OSS code licensed under the GPL. Tesla uses a high percentage of OSS in their vehicles. It is standard for embedded software to contain portions of the Linux kernel or tools, such as Buildroot, which is GPL licensed, requiring that the licensee OS their software under certain conditions.
Software Composition Analysis (SCA) tools should be a valuable solution to address this challenge by automating the process of scanning software projects, identifying the open source components used, and analyzing their licenses and associated obligations. An SBOM (software bill of materials) can be generated and provided to organizations to help manage their usage and ensure adherence. A comprehensive SBOM for OSS adherence includes:
- Component Identification: All the OSS components used in the software project, including the component name, version ranges, and specific release and build details.
- License Information: specifies the license(s) under which it is distributed with proof of provenance.
- License Obligations: A detailed and exact overview of the license obligations for each component. It outlines the specific actions and responsibilities required to fulfill and comply with the respective licenses. These obligations may include requirements such as attribution, sharing modifications, providing access to source code, and ensuring proper distribution of the license text.
- Dependencies: capturing the dependencies between different OSS components. Highlighting how components are interconnected and reliant on one another. Understanding these dependencies is essential for assessing the impact of license obligations and ensuring adherence throughout the software project.
- Source Code Locations: includes the locations of the source code for each OSS component. This aids in complying with licenses that require sharing or providing access to the source code upon request.
- Metadata and Descriptions: metadata and descriptions for each OSS component, including project URLs, maintainers, descriptions, and any relevant notes or comments.
- File-Level Information: provides granularity in understanding which specific files, components, embedded assets, or snippets within a component are in use.
- License Compatibility Analysis: provide compatibility between different licenses and provide guidance on any potential conflicts or restrictions that may arise when combining various components within a single application.
- Policy Enforcement and Remediation: enable organizations to define and enforce their policies and guidelines for adherence by offering mechanisms for flagging non-compliant components, automating remediation processes, and integrating with development workflows to ensure adherence from the early stages of software development.
Among the various attributes of an SCA tool, the accuracy of the data stands out as the most crucial factor and is inadequate without this essential component. Accuracy is the fundamental aspect that determines the effectiveness and completeness of the solution. Without accuracy and proof of provenance (the original author) in OSS adherence, an SCA tool becomes incomplete and inadequate in fulfilling its intended purpose and leaves organizations to manually check the provided origin of each component or, in more concerning scenarios, relying on potentially inaccurate data provided by the tool, assuming it is correct.
During a proof of concept, the following capabilities should be presented:
Granular License Compliance: components can be used in different parts of a codebase, and each component or snippet may have its own license. Snippet-level license detection enables organizations to precisely identify the licenses applicable to specific code snippets and ensures adherence to the associated obligations and restrictions. Without this capability, your organization will be put at risk for compliance violations.
Proof of Provenance: provides a link referring to the one true origin or lineage of each author of the OSS artifact.
- Licenses can change over time or have version updates, further emphasizing the need for accurate license identification. The GNU General Public License (GPL) has multiple versions. Each version may have different terms and conditions.
- May be subject to amendments or updates by the license steward or governing body. These changes can introduce new obligations or modify existing ones.
- Evidence of the origin and legitimate use of the components helps organizations defend against claims of copyright infringement or licensing violations.
- By demonstrating transparency in the sourcing and usage of components, organizations can build trust with customers, partners, and regulatory authorities.
- Certain industry regulations, such as those in the healthcare, financial, or government sectors, require organizations to demonstrate adherence to specific software sourcing and licensing requirements. Proof of provenance helps organizations meet these regulatory obligations by providing documented evidence of the origin and adherence status.
- Enables organizations to ensure that the components they are using come from trusted sources and have the necessary licenses and permissions for use.
Custom Licenses: Some organizations create custom licenses to meet specific business requirements or to protect their intellectual property. These custom licenses may have unique terms and conditions that are not covered by standard OSS licenses.
Accurate License Attribution: correctly attribute licenses to specific code snippets or components within the codebase. It should provide granular information about which parts of the code are subject to which licenses, facilitating precise license adherence and management
Robust Scanning and Analysis: capable of thoroughly scanning, analyzing, and detecting open source within the entire codebase. It should efficiently handle large-scale projects and detect components and licenses across multiple layers of dependencies, accurately capturing the entire software composition, including dependency managers, archives, open source files, copied code snippets, AI-generated code from ChatGPT, Github Copilot, embedded scripts, CDN references as well as many more.
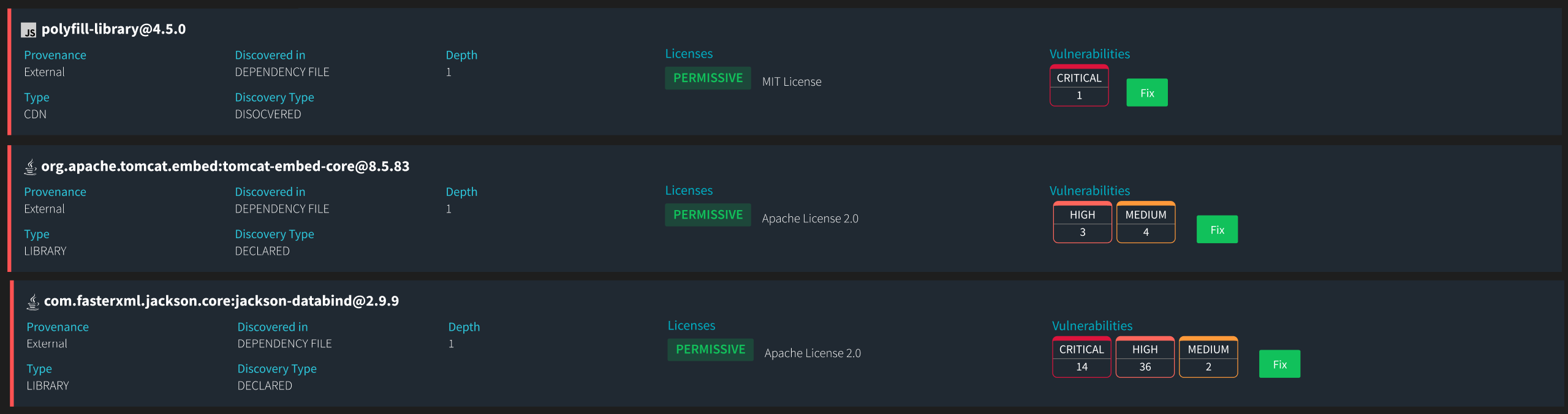
Updated Vulnerability Information: The ability to identify known vulnerabilities associated with components by providing the latest vulnerability information, including severity levels, CVE (Common Vulnerabilities and Exposures) identifiers, and suggested and automated remediation actions.
Continuous Monitoring and Updates: Continuously monitors for new vulnerabilities and updates to licenses with mechanisms to stay informed about changes in license terms or the discovery of new vulnerabilities, allowing organizations to proactively address adherence issues and security risks.
In the realm of SCA tools, Threatrix stands apart, offering unmatched snippet-level license detection with a proven 98% accuracy that surpasses every solution on the market. Its granular attribution, cutting-edge vulnerability management, comprehensive build time scanning, and continuous monitoring capabilities set the new gold standard in open source license compliance.
With Threatrix, organizations gain unprecedented confidence in their adherence program, mitigate risks effectively, and stay ahead in the ever-evolving world of AI-generated code snippets by your development teams. Experience the unrivaled accuracy of Threatrix and elevate your software composition analysis solution to new heights.