In software development, where the fusion of creativity and technology crafts the backbone of the digital world, the quest for maintaining legal compliance and security amidst a sea of open-source integration has never been more pivotal. A Software Bill of Materials (SBOM) is a crucial report in this landscape, offering an exhaustive list of all software components.
However, the true efficacy of an SBOM isn’t a subpar tool that creates a report; it is the accuracy of the data provided, especially regarding snippet-level license detection with the use AI development tools. As AI systems become increasingly complex and integral to business operations, the need for transparency in software components becomes more crucial.
A critical example of what happens with a misstep of license compliance brings us back to 2018 when Tesla released a portion of its Autopilot intellectual property because it was using open source code licensed under the GPL. Tesla uses a high percentage of OSS in its vehicles. It is standard for embedded software to contain portions of the Linux kernel or tools, such as Buildroot, which is GPL-licensed, requiring the licensee to open source their software under certain conditions.
The Indispensable Role of Accurate SBOMs
An SBOM is fundamentally a visibility tool, allowing stakeholders to delve deep into the software’s architecture to identify every open-source or proprietary component. This transparency is crucial for security, compliance, and maintaining operational integrity.
However, more than the mere listing of components is required. The SBOM’s utility is significantly diminished if the underlying solution inaccurately identifies components or fails to detect all associated licenses. Such inaccuracies can mislead users, leading to compliance oversights and potential security vulnerabilities.
IDE Developer Plug-in for Compliance
Introducing an IDE plugin for compliance, exclusively provided by Threatrix, marks a significant advancement in integrating open source compliance into the software development lifecycle. This is a game-changer for organizations, significantly enhancing efficiency and adherence to compliance standards set by compliance teams without hampering developers’ creative flow.
It saves organizations considerable time and improves overall compliance by empowering developers to identify and address compliance issues at the moment of creation, based on company policies, rather than later in the supply chain.
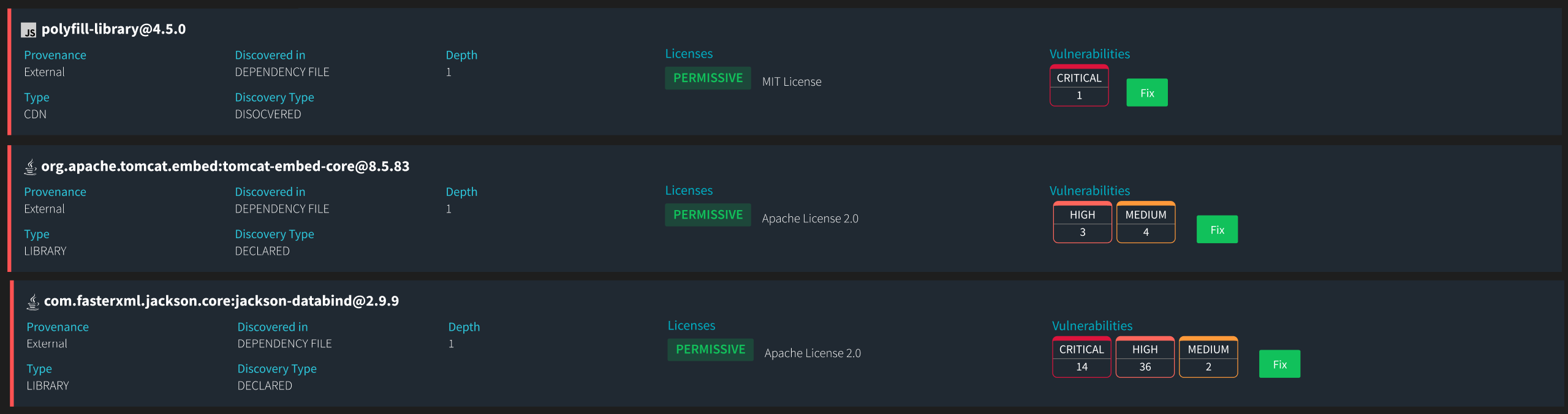
Why Snippet-Level License Detection is Critical
In open-source software, licenses dictate the terms of usage, modification, and redistribution. Misunderstandings or oversights regarding these licenses can lead to substantial legal and operational risks.
When managing code snippets within a software project, the accuracy of a solution that identifies specific licensing requirements is crucial. Code can be sourced from various sources in software development, including open-source libraries, third-party vendors, or internally developed repositories. Each of these snippets may come with multiple legal and compliance obligations based on the license under which it was released.
The precision of license detection and attribution becomes imperative when dealing with AI-generated code, which often amalgamates snippets from various sources, each potentially governed by different licenses. Without this granularity, developers might inadvertently include code in their projects that violates licensing agreements or exposes their products to security and legal risks.
Proof of Provenance
In software development and use, licenses attached to open-source components can often change over time due to updates, modifications, or changes in ownership. This variability can lead to challenges in compliance if not accurately tracked.
Threatrix addresses this critical issue by embedding a feature in its dashboard that allows users to verify the original author of the licenses. When users interact with the dashboard and click the “origin” button, they are linked directly to an external web page displaying proof of the original author.
This functionality provides definitive evidence of the license’s origin, helping organizations adhere to the correct and current licensing requirements. This proof of provenance is essential for maintaining legal compliance and mitigating risks associated with software licensing in the ever-evolving landscape of open-source software use.
By providing this critical information, users are informed of the licenses’ details, can verify their authenticity, and track any changes over time. This capability enhances trust and accuracy in license management, safeguarding organizations against potential compliance issues.
Without proof of provenance (the original author) in OSS adherence, an SBOM is incomplete and inadequate in fulfilling its intended purpose. It leaves organizations to manually check each component’s provided origin or, in more concerning scenarios, rely on potentially inaccurate data.
Enhancing the Value of an SBOM
The significance of the accuracy of the information in SBOMs lies in the necessity for a robust software supply chain security and compliance solution that includes meticulous analysis and accurate reporting of every software component. This ensures comprehensive visibility and control over software inventories, crucial for managing and mitigating associated vulnerability and compliance risks.
A software supply chain security and compliance solution should include the following:
- Robust Policy Management: Automated policy management and an IDE plugin for policy enforcement, guiding developers toward compliance without disrupting the creative process.
- Advanced Detection Features: Identifying AI-generated code and manually copied snippets.
- Vulnerability Remediation: With Auto-Fix capabilities, the solution doesn’t just highlight problems; it provides solutions, streamlining the path to compliance and security.
- Unlimited Scans: Threatrix allows for continuous, real-time, unrestricted scans of codebases, ensuring all components are consistently monitored for compliance and security.
- CI/CD and SCM Integration bridges the gap between rapid development and strict compliance adherence by seamlessly integrating with existing pipelines and Source Code Management systems.
- Flexible Deployment Options: Whether operating in cloud environments or on-premise, Threatrix adapts to different infrastructural needs, ensuring seamless and effective compliance efforts.
- Comprehensive Scanning Capabilities: From source code to containers and CycloneDX frameworks, Threatrix covers every aspect of software scanning, ensuring no component is overlooked.
- Extensive Language Support: Covers more than 420 programming languages, ensuring comprehensive coverage regardless of the project’s complexity or diversity.
- Developer-Centric Tools: A user-friendly dashboard and GraphQL API enhance accessibility and usability for developers, embedding compliance into the daily workflow.
- Workflow Customization: Features like scoped actions, action-driven policy builders, and policy-driven actions allow teams to tailor their compliance workflows to their specific needs, enhancing efficiency and effectiveness.
- License Obligations and Restrictions: More detailed information on the specific obligations and restrictions associated with each component’s license, including compatibility between different licenses and guidance on any potential conflicts or restrictions that may arise when combining various components within a single application.
- File-Level Information: provides granularity in understanding which specific files, components, embedded assets, or snippets within a component are in use.
In the intricate dance of modern software development, where AI and open-source components play pivotal roles, an SBOM backed by Threatrix is not just helpful—it’s essential.
Threatrix ensures that every software component is scrutinized for compliance and security, making the SBOM a dynamic tool that not only reports on what’s inside the software but also secures and streamlines the path toward full compliance. With Threatrix, organizations can confidently navigate the complexities of today’s software development landscape, ensuring that innovation and compliance go hand in hand.