Software development is evolving at a breakneck pace, with developers under increasing pressure to deliver projects faster and more efficiently. As a result, they are turning to tools like StackOverflow, Unity Answers, Github, and AI-based tools like ChatGPT and Github co-pilot to reduce development time and improve efficiency. These AI-based tools improve developer efficiency, and their use is increasing quadratically. As these trends accelerate, companies are caught off guard with no way to measure and respond to the security and license risks of using embedded open source software.
The traditional supply chain carries the risk of embedded malware, prompting companies to shift towards using source-based components to limit supply chain risk. This shift, coupled with the increasing use of AI tools and training on open source projects, leaves companies unprepared.
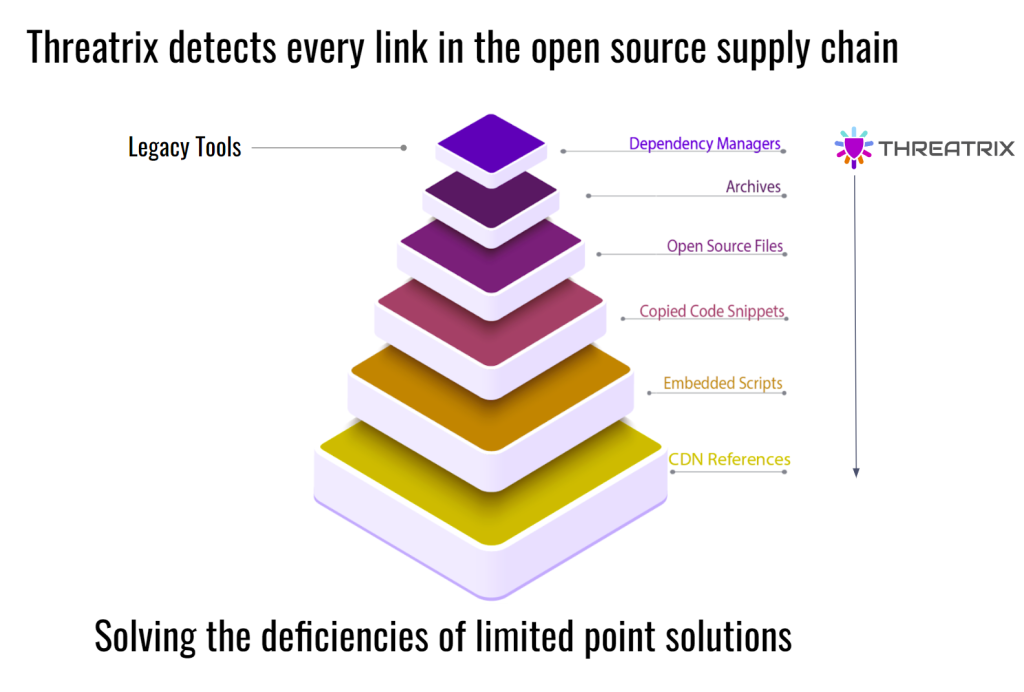
While existing Software Composition Analysis (SCA) tools focus on whole components declared in dependency managers, they are incapable of detecting the various ways developers use open source.
Enter Threatrix – the only solution capable of quickly and accurately detecting open source in every way a developer chooses to use it, from dependency manager data down to CDN references and beyond.
Our TrueMatch technology with Origin Tracing provides proof of provenance with every result, ensuring pinpoint accuracy, low false positives, with immediate actionable results.
With an unparalleled breadth of detection, build time results, massive scale, end-to-end automated risk remediation, and license compliance, Threatrix stands alone in the SCA landscape.
With the rapidly changing landscape of software development, companies need to take a proactive approach to manage security and license risks associated with open source. Threatrix provides the most comprehensive and effective solution in the market, empowering development teams to work more efficiently and confidently without sacrificing security or compliance.


