The recent exploit with the malicious polyfill library highlights a critical gap in the capabilities of most Software Composition Analysis (SCA) tools. Widely used to ensure compatibility across different browsers, Polyfills can pose significant security risks when hosted on Content Delivery Networks (CDNs).
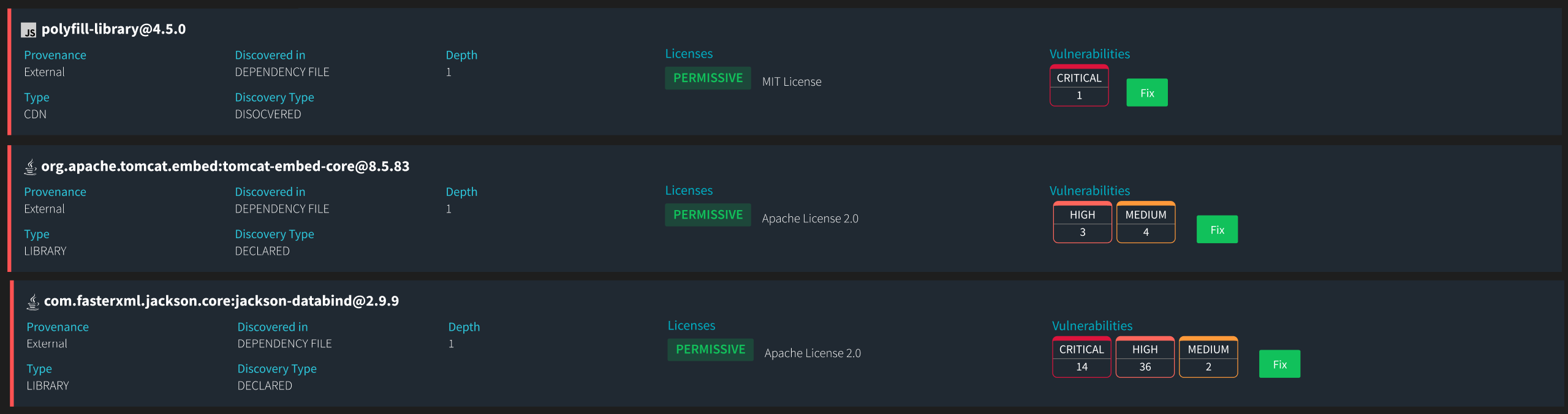
Threatrix has long supported the security of CDN-referenced open source, detecting a wide range of open-source components and assets often missed by other SCA tools, thereby closing significant security gaps.
What Happened with the Malicious Polyfill Library?
A malicious polyfill library recently infiltrated the JavaScript ecosystem, exploiting developers’ trust in polyfills to ensure cross-browser compatibility. This exploit exposed the vulnerabilities of relying on CDNs to host such libraries, as malicious actors can propagate harmful code through numerous applications.
What is a JavaScript Polyfill?
A JavaScript polyfill is a piece of code (often a library) used to provide modern functionality on older browsers that do not natively support it. Polyfills enable developers to write standard-compliant code without worrying about browser inconsistencies.
The Role of a JavaScript CDN in Polyfill Libraries
CDNs play a crucial role in delivering polyfill libraries efficiently across the globe. They ensure that the content is quickly and reliably accessible to users. However, this reliance on external CDNs introduces security risks, as compromised libraries on a CDN can affect all applications that reference them.
Security Risks of Polyfills Hosted on a CDN
Polyfills hosted on CDNs can be tampered with, introducing malicious code into applications. This risk is compounded by traditional SCA tools often overlooking CDN-referenced open-source components, leaving a significant portion of the application’s codebase unmonitored and vulnerable.
Why Upgrade Your SCA Tool?
Threatrix has always supported CDN-referenced open-source security. Using SCA tools that ignore open-source is asking for trouble, as most miss up to 40% of the open-source your developers use. Upgrading components is essential, but upgrading your SCA tool is more crucial.
Comprehensive Detection Capabilities
Threatrix’s supply chain security platform detects far more open-source components and assets than competitors, including:
CDN References:
- Many SCA tools fail to monitor open-source libraries referenced through CDNs, leaving a significant blind spot. Threatrix continuously scans and monitors CDN-referenced libraries, immediately identifying and addressing any vulnerabilities or license issues within seconds of a scan.
Embedded Snippets:
- Open-source code can often be copied and embedded directly within a proprietary codebase. Threatrix’s sophisticated scanning algorithms can detect these embedded snippets, regardless of their location within the code, ensuring comprehensive coverage.
Forked Repositories:
- Developers often fork open-source repositories to customize or enhance functionality. These forked versions may diverge significantly from the original, potentially introducing new vulnerabilities. Threatrix tracks these forks and assesses their security and license compliance.
Source Files:
- Beyond packaged libraries, individual source files may contain open-source code. Threatrix meticulously scans these files to ensure all open-source code is detected and evaluated.
Binaries:
- Open-source components can be included in compiled binaries, which many SCA tools overlook. Threatrix’s binary analysis capabilities allow it to dissect these binaries and identify the presence of open-source components, providing a complete picture of the software composition.
Dependency Managers:
- Threatrix integrates with various dependency management tools (like npm, Maven, etc.) to analyze and track dependencies across multiple projects and languages, ensuring that all open-source components are accounted for and assessed for risks.
Archives:
- Threatrix scans archived files (e.g., ZIP, TAR) to detect and analyze the open-source components they contain, ensuring no code escapes scrutiny.
Empower your vulnerability detection with unmatched control and risk visibility thanks to the unparalleled capabilities of Threatrix’s TrueMatch technology, which identifies concealed open-source components often overlooked by other SCA tools.
Securing Your Team Against Attacks
Threatrix provides four essential ways to protect your teams:
- Supply Chain Risk Score: Our supply chain risk score informs developers when a referenced artifact poses a risk based on various factors within the composite Supply Chain score. For instance, the malicious polyfill library would trigger numerous red flags, immediately notifying our customers of associated risks. Alerts based on supply chain risk scores help your team identify potential threats before integrating the code into your product.
- Vulnerability Reporting: Polyfill is reported as a vulnerable component, alerting developers to the risks associated with using it in their projects.
- Continuous Monitoring and Updates: Threatrix continuously monitors open-source components, automatically updating its database with the latest vulnerability information and license changes. This ensures that developers are constantly working with the most current data.
- Autonomous Mode: Threatrix manages the compatibility and upgrading of open-source components by evaluating their compatibility within your codebase. This includes assessing dependencies, identifying potential conflicts, and ensuring all components work seamlessly together. This effectively reduces the developer workload by over 90% and significantly minimizes technical debt.
When new versions of components are released, the autonomous feature determines their compatibility with your existing codebase and automatically upgrades them. This proactive approach ensures that your software always uses the latest, most secure, and most efficient versions of open-source components.
By keeping all components up-to-date and ensuring compatibility, Threatrix significantly reduces technical debt. This prevents the accumulation of outdated, insecure, or inefficient code that can slow development and create security risks.
It’s crucial that your supply chain security platform comprehensively detects all open-source components used by your development team. Otherwise, you’re leaving gaps in your security posture that threat actors can exploit through Polyfill-style attacks.
As these specific attacks become more prominent and sophisticated, it is essential to use a security platform like Threatrix, which can detect and help your team immediately respond to these advanced threats.

