Open-source software fuels innovation, but its “free” nature comes with obligations that many businesses ignore—often to their detriment. Compliance isn’t about checking off legal boxes; it’s about protecting your business from hidden risks lurking beneath the surface of your codebase. If you don’t know what’s in your software, you don’t know what you’ve agreed to.
Ignoring open-source compliance can lead to lawsuits, product recalls, and security vulnerabilities. If that doesn’t concern you, consider this: 84% of open-source codebases contain at least one known security flaw, many of which remain undetected for years [How Threatrix Ensures Open Source Security and Compliance]. In an industry that moves fast, companies that fail to manage their open-source exposure put themselves at risk of catastrophic failures, delays, and compliance nightmares.
The Role of Legal and Compliance Teams in Open Source Management
Open-source compliance is not just a developer responsibility. Legal and compliance teams play a critical role in ensuring that companies use open source software in a legally sound and risk-free manner. While developers focus on writing and integrating code, legal teams must:
- Review and approve open-source usage policies.
- Ensure compliance with corporate governance and industry regulations.
- Work with security and engineering teams to prevent compliance violations.
- Assess risks associated with third-party dependencies and licensing terms.
The Reality of Open Source Licensing
Every piece of open source software comes with a license, granting specific rights and imposing obligations. You don’t get to pick and choose which rules apply. Once you use open source, you inherit the terms—knowingly or not. It’s not just about whether you comply; it’s about whether your customers and partners can. If your software incorporates code under restrictive licenses (e.g., AGPL), your users could be legally bound by those terms. That’s a liability most businesses can’t afford to overlook. [Understanding Open Source Licenses and Their Impact].
The Hidden Risks of Ignorance
Modern development hides complexity. Dependencies are pulled in automatically. If you don’t actively manage your open-source exposure, you’re flying blind. This has serious consequences:
- Legal vulnerability – License non-compliance can lead to lawsuits and forced open-sourcing of proprietary code.
- Security blind spots – Vulnerabilities in untracked dependencies can be exploited.
- Operational chaos – Inadequate tracking leads to compliance bottlenecks and last-minute fire drills.
Why Open Source Compliance Feels Overwhelming
One of the biggest challenges in open source compliance is the disconnect between legal and development teams. Developers focus on building features and integrating code quickly, while legal teams are concerned with risk management, license compliance, and contractual obligations. This lack of unity creates compliance gaps.
- Legal teams often lack accurate insights into what open source components developers use due to the limitations of most Software Composition Analysis (SCA) tools. The biggest challenge is that these tools struggle with accurate author attribution, leading to false positives and incomplete license tracking. Threatrix, with its 99% snippet-level accuracy, eliminates these blind spots, ensuring legal teams have precise and actionable data to assess risks in real-time.
- Developers may not fully understand licensing requirements or compliance obligations, leading to accidental violations.
- Security and compliance audits become reactive rather than proactive, creating additional pressure in fast-paced release cycles. Development teams are already working under tight deadlines, and compliance issues that surface late in the process force last-minute fixes, diverting valuable resources and delaying product launches. The constant balancing act between speed and compliance creates friction, making it harder to integrate necessary compliance checks seamlessly into the workflow.
- Time-Consuming Manual Audits: Without automation, compliance reviews slow down development cycles and create bottlenecks.
- Security Exposure: Unknown dependencies increase attack surfaces, making organizations vulnerable to cyber threats. Many compliance frameworks require organizations to manage and document third-party code usage.
The Cost of Non-Compliance
A Costly Mistake: Major Tech Company’s Licensing Violation
A notable example of the consequences of GPL license violations is the case between Entr’ouvert and Orange S.A. In February 2024, the Paris Court of Appeal ordered Orange to pay over €900,000 in damages for infringing on the GNU General Public License (GPL) version 2.0. The court found that Orange had violated the terms of the GPL by incorporating open-source software into their proprietary products without adhering to the license’s conditions. This case underscores the legal and financial risks companies face when they fail to comply with open-source licenses. [Read more]
Artifex vs. Hancom: A Cautionary Tale
In 2017, Artifex, the creator of Ghostscript, sued Hancom, the developer of an office suite that included Ghostscript. Artifex offers two licenses for Ghostscript: the AGPL and a commercial license. Hancom failed to obtain a commercial license and did not release its office suite as free software, violating the AGPL terms. Artifex sued Hancom in U.S. District Court, where the court ruled that the AGPL license was enforceable and that Hancom had breached contract terms. This case reaffirmed that open-source licenses are legally binding agreements and non-compliance can result in serious legal consequences. [Read more]
Intelligent Open Source Compliance
1. Know What You’re Using
Most organizations don’t have a complete inventory of their open-source usage. You need real-time visibility into what’s inside your software—not just top-level dependencies but every single component. This includes tracking all direct and indirect open-source components, their versions, and any modifications to ensure complete awareness of your supply chain. [Best Practices for Managing SBOMs in Open Source Compliance].
2. Understand What You’ve Agreed To
Simply tracking components isn’t enough. You must understand the licenses that govern them. Each license may impose specific requirements, such as attribution, restrictions on commercial use, or obligations for disclosing modifications. Some licenses may conflict with your business model, while others may lack clear authorship, making attribution difficult. Developers often overlook these terms until it’s too late. Therefore, knowing the details of your open-source agreements is essential to maintaining compliance. [Open Source Compliance in the Enterprise – Ibrahim Haddad, Ph.D.].
3. Proactively Assess Risk
Not all open-source components are created equal. Some licenses carry restrictive obligations that may conflict with your business model, while others lack clear authorship, making attribution difficult. Many open-source libraries also have outdated codebases or unresolved security vulnerabilities, increasing the risk of breaches.
Before integrating an open-source component, consider the following:
- License Restrictions – Does this license require public disclosure of modifications, impose copyleft obligations, or restrict commercial use?
- Security Health – Does the component have active maintainers, recent updates, and a history of patching vulnerabilities?
- Dependency Chain Risks – Does this component introduce indirect dependencies with their own compliance risks?
- Legal & Operational Alignment – Can your legal team approve this software without extensive review? Will it scale with your product roadmap?
4. Build Compliance Into Your Process
Compliance isn’t a one-time audit; it’s an ongoing responsibility. It should be woven into your development lifecycle through continuous integration/continuous deployment (CI/CD) pipelines and automated compliance tools. Threatrix enables this by providing:
- Automated Compliance Checks in CI/CD Pipelines – Open source components are scanned in real-time before they are deployed, ensuring compliance without disrupting development workflows.
- Drag-and-Drop Project Analysis – Teams can quickly analyze entire codebases by dragging and dropping projects into the Threatrix platform. This feature is especially useful for auditing existing projects, onboarding new codebases, or conducting one-off compliance reviews before integration into production workflows, ensuring compliance without disrupting active development cycles.
- Immediate Feedback for Developers and Legal Teams – Potential violations are flagged instantly, allowing legal and security teams to take action before non-compliant code is merged into production.
By integrating compliance into the development process before a project begins, companies can avoid costly rework and maintain complete visibility into their open-source usage.
- Legal teams review and approve open-source usage.
- Developers receive compliance training and understand policy guidelines.
- The new code is checked for license conflicts before it’s merged.
- Security and compliance teams collaborate on an ongoing risk mitigation strategy.
The Threatrix IDE Plugin: A Gamechanger for Open Source Compliance
Traditional compliance approaches are slow, reactive, and disconnected from the development process. This is where the Threatrix IDE Plugin changes the game.
With real-time license detection and compliance enforcement directly within the developer’s workspace, Threatrix ensures that legal teams aren’t the last line of defense—compliance starts where the code begins.
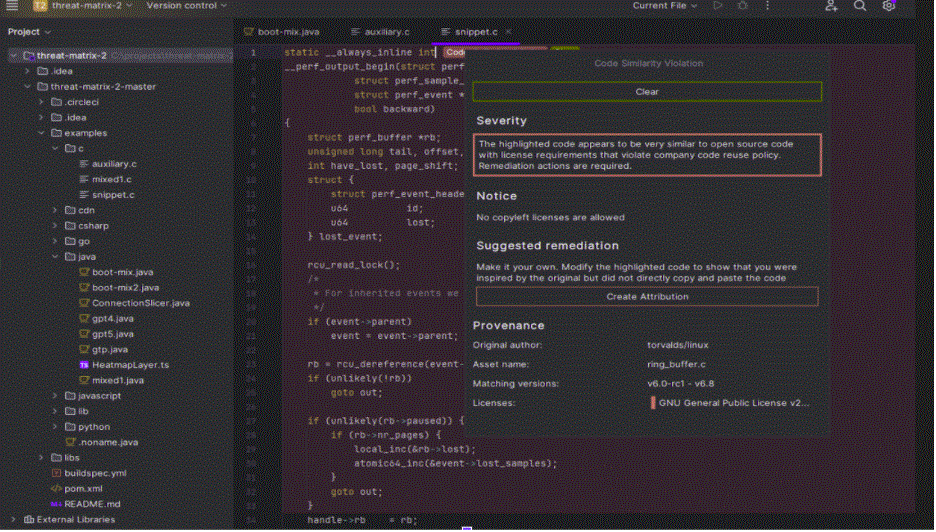
Why It Matters:
Automated Copyright Notice Insertion – Developers don’t need to track when copyright notices are required. The Threatrix IDE Plugin automatically adds the required copyright notice in the file header, ensuring compliance without interrupting the development process.
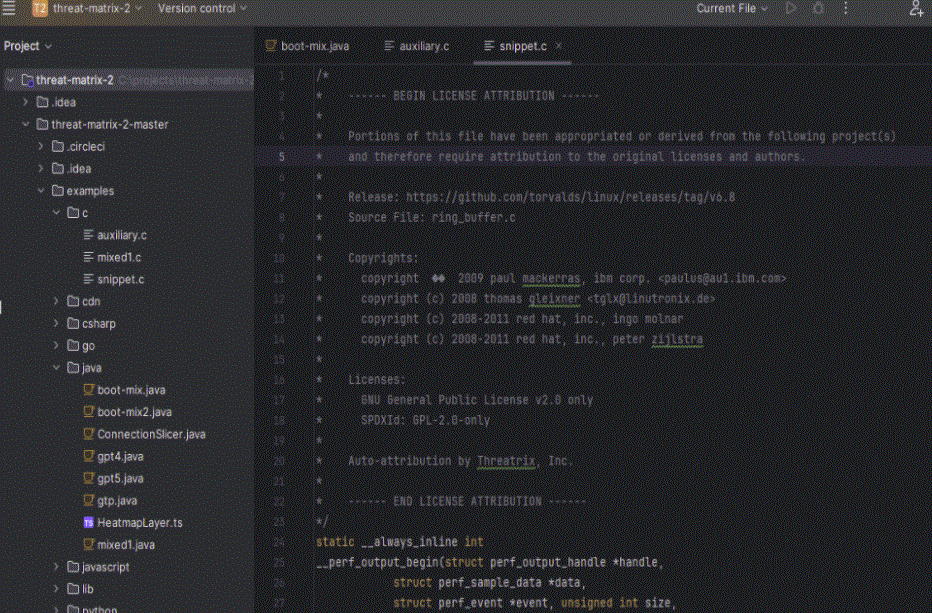
Instant License Checks – Developers get real-time alerts about licensing conflicts before code is committed, reducing costly rework.
Snippet-Level Detection – Threatrix identifies even tiny fragments of open source code, ensuring compliance down to the most granular level.
Seamless Collaboration – Legal, security, and engineering teams work together effortlessly, using Threatrix to maintain compliance.
Automated Policy Enforcement – Companies can configure custom license policies, ensuring only approved open-source components are used.
Reduces Manual Audits – Say goodbye to endless legal reviews—Threatrix ensures compliance at every stage of development.
With Threatrix, open source compliance is no longer an afterthought—it’s a cross-functional effort between legal, security, and development teams. Real-time monitoring, automated enforcement, and seamless collaboration ensure compliance without slowing down innovation.
If you don’t know your obligations, you’re already behind. Take control of your open-source exposure before it controls you—with Threatrix.

